When you attempt to run the WordPress core updates you receive the following error: “Error: Could not connect to the server. Please verify the settings are correct.”
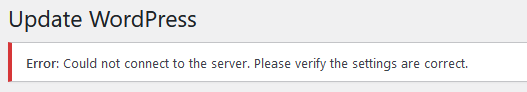
Check and see if only two settings are available, “FTP” and “FTPS”. A more secure option is SSH2 which is supported by most Apache systems but this option is not visible in WordPress.
In order to add the SSH2 option, you will need to access the server shell and install “php-ssh2“. The command is “sudo apt install php-ssh2“.
Once php-ssh2 is installed, restart the Apache service using: “sudo systemctl restart apache2“.
Go back to WordPress and refresh the page, you should now see the below:
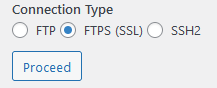
Enter your normal user credentials and select “SSH2” and click proceed. The update should now work as expected. You do not need to enter the authentication keys unless you set these up previously.
If it doesn’t and you receive “Could not create directory. Installation failed.” this means that your folder permissions are not set correctly for WordPress.
In order to fix the file and folder permissions use the following commands:
sudo find . -type f -exec chmod 664 {} +
sudo find . -type d -exec chmod 775 {} +
sudo chmod 660 wp-config.phpSome server configurations do not permit the wp-config.php file to be set to 660, it will result in the site becoming in accessible. If this is the case in your situation, change the permissions to 664 and this should resolve the issue (It adds the “read” permission back for guests).
